CPTC Nationals in Rochester, NY
Table of Contents
Overview
[...] CPTC is a bit different from several other collegiate Cybersecurity competitions. Instead of defending your network, searching for flags, or claiming ownership of systems, CPTC focuses on mimicking the activities performed during a real-world penetration testing engagement conducted by companies, professional services firms, and internal security departments around the world. (via cp.tc)
I was "team captain" for our CPTC team for the 2021-2022 event. We qualified for Nationals (Globals?), but didn't place in the top three. This was my first (and last!) time at the Nationals event-- I'll be writing about the experience, and particularly, anything I wasn't expecting.
If you're unfamiliar with CPTC, think of it like CCDC, but red team. If you don't know what CCDC is, it's like a weekend of pain and suffering, except for no tangible gain. But I keep coming back, because I like the way it hurts.
What exactly /is/ this competition? What is penetration testing? Who is 'CCDC'?
Computers, and networks of computers together (like you might see at your job or school), are horrifically complex. This means there are a lot of problems with them that often go unnoticed. Penetration testing (or 'pentesting') is a more professional way of saying "hacking," as it is conventionally understood by the general populace, and is meant to uncover these flaws before they are taken advantage of by someone with bad intent (worse than charging them money, in any case).
CPTC is a college competition where students get realistic-ish-kinda experience by pentesting a fake computer network. CCDC is a similar competition, except you're on the defensive, rather than the offensive.
If that paragraph is totally nonsense to you, the rest of the post may be difficult to follow.
I hate to love and love to hate the soft skills emphasis of this competition. It's always interesting to see how socially inept and unprofessional my communications are in hindsight, after writing them and thinking they were super on-point. It's very tough to write everything cleanly and authoritatively while also walking on eggshells, which is what you have to do. And I don't know if there is a professional way to write an email asking for them to restart a service after we dumpstered it for the eighth time.
Or, as an in-person example, some of us were sloppy and did a light scan on the whole network, rather than excluding the two SCADA systems they asked us to. They came by the room to reem us, and when they asked if anyone had hit those boxes, I was like "I don't think so, did you guys?" who of course just shook their heads. That seemed reasonable to me, but as they mentioned later, it came off as unprofessional and lazy-- the correct response would have been, "I don't believe so; let me check our records and get back to you within
RFP
Some questionable planning decisions left our team with only a day to complete the RFP. Last year's team (which I didn't try out for) didn't get together until a week after the RFP submissions opened, and they weren't able to get into our region. So we cranked. Luckily, thanks to my high school experience, I am an expert at spewing BS. I was able to re-use some pre-spewed crud from another event (that we didn't get into, thanks Social Engineering CTF), which sped up the process. Nothing really more to say on this, no surprises there.
Regionals
OSINT
I hate "advanced" OSINT. It's always one tiny crumb on a trash website behind a auth-wall that leads to another, to another, to another, with maybe a couple of super "logical" guesses to jump some gaps. It's just not fun at all.
We (read: exclusively my teammates) found a user account, a StackOverflow post, and a hidden drive folder of "Zoom recordings", all of which were almost 0% helpful. The "Zoom recordings" gave me ulcers and mentioned a password for Jim Joseph, which was valid approximately nowhere. I think we got more credit for including those results on our report and on the inject than we did from the content itself.
I'm sure there was some way to apply the information, but I would be surprised if there was anything game-changing out there. In 2019, there was a valid SSH key out there, which was actually useful, and I was expecting something like that.
Infrastructure Issues
For our area (Central), the Regional CPTC event was on October 23rd, 2021. I rolled out of bed, and directly into my chair (no standing, to minimize calories expended). And...
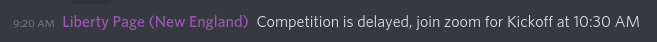
Ok, false alarm. A bit more sleep. Round two, as soon as the competition started, I launched my Wireguard VPN, and...
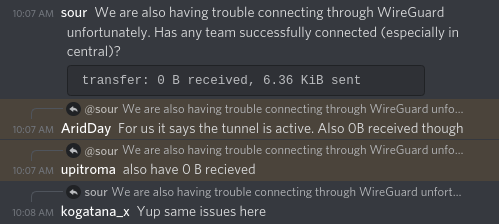
Okay, maybe it's just a couple of us...
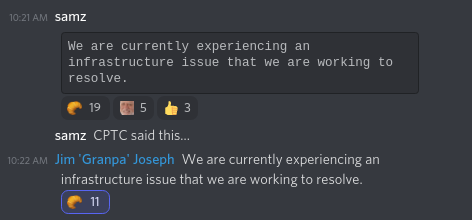
This was the first of a long series of infrastructure problems. If I had to summarize this competition in one word, I would say "fun," and closely after that, "infrastructure-issues." And if I had to pick a third, "last-minute-report-writing."
I help run competitions for our school's security club, and we've had our fair share of infrastructure issues. Unfortunately we are stuck with vSphere, and sometimes, it really, honestly, actually, just craps out. I'm sure there's a deterministic explanation at some level, but we are not empowered to discover it due to our low permissions and the closed-source nature of the product (that's right, I'm still FOSS shilling).
The CPTC team writes all their infrastructure tooling from the ground up (with LaForge)-- or as much ground as possible when building on the cloud-- and they were planning on hosting through the RIT cyber lab, but for Regionals (and spoiler, Nationals too), they reverted to using AWS and some old scripts. We didn't know this until afterwards, though. I don't think they ever told us the root cause, other than just exceeding their allocated resources (which seems like a tractable problem).
Anyway, who am I to complain, stuff happens.
Actually "Pentesting"
As soon as we got into the environment, we ran our nmap scans and began gobuster-ing instantly, because that's the How You Play HackTheBox.EU™. An hour later, after we had a decent handle on the network, we find that most of the API endpoints are trashed. They're all returning 502s (gateway error) or 403s (forbidden).
Sike, more infrastructure concerns
For one of them, we found some endpoints that seemed to be valid (i.e., returning 200s) through gobuster, but are now, in fact, toast. We briefly considered the possibility that we took them down, but nobody ran anything crazy, just a standard gobuster. If that took down their API endpoints, they were running on potato batteries in series and their web servers were proudly written in Scratch. Or maybe just nodejs.
Alas, as we wouldn't find out until Nationals, we were in fact the cause. I don't know for sure, but from one of their emails, I suspect there was some database-handling code that had its spinal cord explode if you opened more than X concurrent connections, or X connections in close succession. Which seems hard to implement unless you were doing it on purpose, so it's probably something else.
I had a wicked theory on what happened-- since we found a MySQL database that was essentially empty, and a PostgreSQL database that had tables but no data, we thought they accidentally changed the database used when rewriting their scripts to use AWS, and so then their database drivers didn't work. But that wasn't it.
Also note that we totally slammed the ESTOP on the SCADA system! Oops! I thought we were stir-fried after that, but we said sorry and the report indicates that we got a "minor bump in credit for handling the issue well."
Writing the Report
As expected, the report was slammed together in two hours whilst eating junk food and trying to force my teammates to actually write any of it.
Awards
I love the anticipation when announcing winners, for anything, really. Winning is great, but even if you don't, you get to experience a wormhole of temperamental perception; did I do great or do I have no chance? Anyway, this was one of those good times, we won our region.
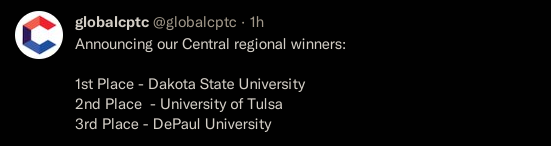
Nationals (Globals?)
CPTC calls their final event "globals", which I suppose is technically true. But I can't bring myself to unironically say "Globals". I feel like Mr. Worldwide. Why not "internationals"?
Traveling to Rochester
Traveling for events is always a lot of fun.

Our lodging was in the RIT Inn, pretty baller to have your own lodge. It was still a 10-15 minute drive from campus though.
I enjoyed the breakfast party every morning. Most of the provided food was fairly good, and everything seemed well-planned. Although there was fair bit of dead time where we just sat around, exploring the facility or talking to people.

It was snowy and either dusk or dawn when we went out. CPTC provided all transportation to and from the hotel. Any food we wanted after 5PM was up to us though.

COVID stuff was kind of a hassle, they needed the results to be in a tight time period, wouldn't accept self-tests, and in typical CPTC/computer nerd fashion, didn't implement any measures to ensure authenticity up front, but just outlined harsh punishments for trying to circumvent it. I showed them the email from my phone, which they accepted.
Actually Pentesting
Shout out to the random RIT students who were in charge of monitoring us during the competition, I don't think I would have lasted the eight hours.

My time was honestly split probably half and half between "pentesting" and just writing emails. I wrote so many emails. There were injects, but usually it was asking them to restart things, if X thing was expected, and so forth. One of my teammates dumpstered his kali box trying to install OpenVAS, I sent an email asking them to revert it, and then he did the same thing five more times.
We were super careful in scanning and probing the network, but we still nuked half the services by the time we finished day two. Time didn't pass as quickly here as it does in other events. It was probably a combination of the team captain/"soft skills" component ruining any opportunity for me to focus for an extended period of time, and the fact that I was just bashing my head against 502's and unexploitable services for the other half of the time.
Professionalism and LARPing
This guy from the Discord made me laugh:
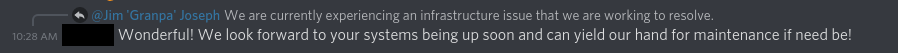
I think it exemplifies a good chunk of issues with "professionalism," especially in this competition.
First of all, it can be ambiguous when you're supposed to be in LARP mode or not. This guy thought Discord communication was in-game (which it technically might be?), and he needed to volunteer his team's services. It can be much worse when you're in person, and someone is dressed like Willy Wonka, but it's outside of competition hours-- how much sucking up is expected (if any)?
The organizers try to simplify it by saying you're always in character, and they scored every interaction over the weekend, but the nature of how you need to interact with the competition organizers blurs that line a lot. You can find yourself stuck between the seams of the simulation. Hello Ms. Wonka, where is the bathroom? Hello Ms. Wonka, are we allowed to ask you to fix your infrastructure? Hello Ms. Wonka, you didn't implement a single thing from our previous report, why did you hire us again?
Secondly, at least for me (and this dude), you tend to default to ⭐overwhelming positivity⭐ as a substitute for profesionalism. No, it is in fact not Wonderful that their infrastructure imploded.
But maybe it isn't about sucking up. Maybe it should be about a natural, respectful relationship between two commercial entities, whose communication is a blissful and elegant dance of likeminded scholars with a laser-focus on business outcomes, execuspeak, and strategic quarterly goals. But honestly that sounds like more of a pain than just sucking up.
We were tasked to give a presentation, in person. Our room's door opened (a sound that I developed a fear response to), and Wonka + Meredith started asking us about insider threats, referring to some news about Ubiquiti. I had no idea what she was talking about, and we slammed together a presentation in literally five minutes. Here was the feedback for it:
Answer was too high level and then went too technical, response was disjointed. [...] Use caution when offering personal opinions (there are places where this is appropriate and ways to soften your approach depending on your rapport with the client).
They also mentioned that you got extra points if you knew about the Ubiquiti Insider threat news, which I didn't (damn you Nickolas).
To be fair, they also said:
Primary point of contact was organized and was well informed, but very technical for an audience with the CEO. Comparison to vertical. Excellent responses to initial question and follow ups.
Which was nice to read. But we still ended up with an 18.6 / 30 score on injects... Well, we actually got a <50% score overall for the entire event, but that's a different issue.
The final presentation, a distilled version of our final report, also required a feat of balancing professionalism. Here were some highlights from that feedback:
Keep eye contact. [I]ncident response [is a] strong word - I would soften [it] to investigate to ensure there isn't an incident. The tldr up front could have been stronger. Recommendations were a bit too positive. Need better time management. You started strong but then didn’t leave enough time for recommendations and questions.
Basically, my point is that I live in front of a computer and "professionalism" is difficult. But you can only improve by practicing, which this competition was great for.
My main takeaways are:
- Simple (even at the cost of losing important detail) is better
- Put yourself in the audience's shoes
- Shoot for 80% of your time slot
- Everybody loves pretty graphics
Report Writing
Report writing can be fun, in the same way that creating a writeup or doing a weblog post about your CPTC experience. It can help you crystalize lessons learned, see patterns, or just give you a chance to write about something fun. But let me tell you what's not fun-- writing a huge report in an hour or two. It seems like such a long time to write a report until there's 30 minutes left and you're still changing the fonts for commands to Consolas.
I would have liked to include a lot more information in the report, and less information in the presentation, but we really only had time for a one-pass of data inputting and a barely one-pass of proofreading, which doesn't lead itself to thorough or eloquent writing. I understand that's the point, but it sucks. I suppose we could've put ourselves in a better spot if we started organizing our vulns found in the document during the pentesting phase, or if I spent less time writing emails and more time on the report, also during the competition time.
Still though, with all things considered, I think it turned out well.
We submitted both the report and the PowerPoint in literally the last thirty seconds. If drag-n-drop into Google Drive didn't work on my Linux Wayland environment, we would've been SOL with the time it takes to use the file picker dialog. Thanks Drew! Not that it matters, because we didn't place, but still... narrow margins.
Our report is up on their report_examples repository (they're supposed to be Anonymous, but I'll give you A hint As to which teAm letter we Are. More recently, they uploaded the presentations slides we Made, however they Mixed up the naMes.). I don't get why they redacted some of our informational graphics though.
Awards
Overall, the CPTC team did a pretty good job supporting hybrid teams. Since the environment was all "cloud"-based, it wasn't too difficult to plan around, but they seemed to stream every event. Wrestling with "the owl" to focus on them was comical at times, but in general it was pretty smooth.

Unfortunately, we didn't win anything lol. Not even the "jackhammer award" (most network traffic sent), which I thought we had in the bag for sure with all those gobuster threads.
We put our stuff in the room they gave us, which automatically locked. We almost missed the bus on the way out, since we had to find someone to unlock it after the awards ceremony.
Side Quest: Feedback Call
About three months after the competition occurred, they reached out to students asking for feedback.
As usual, they were very explicit that I should not use a camera during the call, and I should /not/ tell them what school I'm from. Those instructions, of course, were sent to my school email. Alas...
The suggestions I put together for them were:
- OSINT should be reeled in. Should be reasonable and useful. Red herrings are not fun for anyone (fall2021!).
- Infrastructure problems were more frequent than they should have been. Maybe split up the regions a bit more? Web applications should not be that fragile.
- Network felt like a toy network, the applications didn't do anything useful. Billing "app" with no integration, gift card "service" that's a simple CRUD webapp... Only the SCADABR system felt real.
- Professionalism/constantly in character can be confusing in the context of the competition, for example, asking about competition rules. Normal pentesters are not forbidden from using two monitors or their phones, asking about it can be weird. Same with some infrastructure issues, like if a web application is using an empty database or it exploded after receiving two web requests. Releasing professionalism tallies like the national reports would be helpful.
- Grading was weird. Would receive 5/35 points on something but have overwhelmingly positive feedback. Should normalize that or provide more details. The team said there would be group score percentiles, but there weren't.
Good things:
- Excellent practice for professionalism/socialization. This was the strong point.
- Good in-person logistics and planning.
Epilogue
Scoring feedback.
Snooping around again I see...
Another benefit of the competition, that I didn't discuss above, is the opportunity to scope out likeminded peers, which I find extra valuable since the cyber security realm is so relatively small. "Networking" was very subdued because of COVID vibes, but I still got to meet some cool people, shout out to Cooper and Glen.
This is a blog post from the winning team, which I found interesting. I wish he went more in depth about his Nationals experience rather than how to build a team, but I guess internet strangers can't be choosers.
So, for better or for worse, CPTC shaped up to be a valuable experience. I don't think I learned anything technical, but I learned a lot about professionalism and about being VERY careful in "real" environments. So, I'd recommend it.