HackThePort in Fort Lauderdale, FL
Table of Contents
The Maritime and Control Systems Cybersecurity Con – Hack the Port 22 is a hybrid cybersecurity event by MISI and DreamPort inspired by U.S. Cyber Command. The Conference will be held in Ft. Lauderdale, Florida on March 21-25 at the Greater Ft. Lauderdale Convention Center. (via hacktheport.tech)
When I was asked if I wanted to do 'HackThePort', I thought it would be a cruddy boat-themed CTFd instance meant to recruit for the Navy, maybe with some ICS/signals challenges. I was pleasantly surprised to be mostly wrong!

Overview
This event was a lot of fun (and all expenses paid, without even a single qualifier round). It focused on "exploiting" SCADA systems, which resided on about five separate networks. These were extremely cool, and was my first exposure to this type of technology.
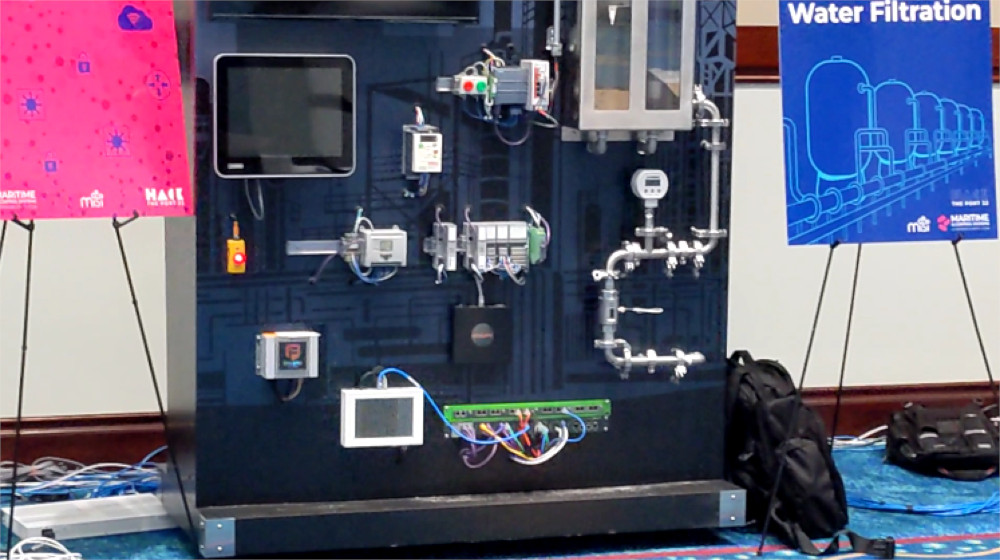
HackThePort (HackThePort 22... no, not SSH) also purported to be a fully-immersive red vs blue team experience, with completely fair grading across three groups tasked to each do a different scenario, several Windows domain exploitation challenges (to pivot to the OT network), a hardware/software implant backdoor on a PC used by blue teamers, an entire network of vulnerable IoT devices and vague directions and rules with what to do with them, a malicious PDF phishing foothold challenge, a physical RubberDucky/BadUSB malware delivery challenge, a fully functional and equivalent remote competitor experience, all on conference WiFi... in four hours each day, for two days total.
If that sentence caused your brain to start melting, that's how it felt being there. The event tried to do way too much, and it was not well designed for an objective, points-based competition. The strength of the event was exposing students to new technologies. The nebulous and constantly expanding competition scope hampered this outcome-- I hardly spent any time actually messing with SCADA systems. But the venue and area was nice!

Organization
The competition was led by a MISI pseudo-god going by the name storyteller. They asked us (three times!) to not take their photo, so I won't reveal any information about the individual out of respect of that request. They emphasized a belief in two competition guidelines:
- Never have a red team challenge without a blue team.
- Letting people loose on the environment is the best way for competitors to get a realistic experience.
The organizational constraints of the competition, or a lack of planning, or miscommunication, unfortunately forced them to compromise or otherwise fail to support these ideals.
It was unclear what was worth points, what was intentionally broken and accidentally broken (a lot), when events started and ended, what we were allowed to do, and so forth. For example, we were visiting the beach after day one, when they sent out an message that there would be an impromptu opportunity that could majorly affect the outcome of the event: come for a tour of the competition space and get a leg up by seeing what devices would be used the following day.
The deadline is simple-- just come before the storyteller left the building. We rushed over, and arrived after everyone else left (or before they arrived, maybe?). Storyteller said, "Hey guys, I'm going to give you the same opportunity as every other team. I'm not going to say exactly what, but," /gestures as if holding phone camera up/, "alright, got it? Let's go." So we followed them, walking around the room, taking pictures and videos of the systems set up. It was helpful, but why so last minute? Why make it a pop-up event rather than something planned? Why be so coy with giving permission to record when it was explicitly mentioned a day earlier? It was this energy, this attempt at strict fairness at the cost of the competition quality as whole, reactive rather than proactive action, that contributed to the event's issues, which seemed designed to be an explorative conference event rather than a competitive one.
It was a six-day event, with one travel day (Sunday), one debrief day (Monday), two scored event days (Tuesday and Wednesday), an unscored/fun day (Thursday), and an awards day (Friday). We were split into three groups, each containing about eight in-person teams and four remote. The schedule looked like this:
Tuesday 3/22
| Time | Group | Scenario |
|---|---|---|
| 0700 | Group 1 | FTZ |
| 1100 | Group 2 | FTZ |
| 1500 | Group 3 | FTZ |
The FTZ, or Foreign Trade Zone, is the challenge network with a bunch of vulnerable IoT devices, and an exposed TCP/Modbus service (presumably controlling some PLC). It also, maybe?, has the machine we were meant to establish persistence on.
Wednesday 3/23
| Time | Group | Scenario |
|---|---|---|
| 0700 | Group 1 | Never Spill a Drop |
| 1100 | Group 2 | Go With The Flow |
| 1500 | Group 3 | Trains-A-Comin |
It's worth noting that the Trains-A-Comin scenario, in their informational packet, which you can read here, is supposed to be magnitudes more difficult than the other two scenarios. We were assigned to Group 2, the easiest scenario. I don't think the groups were divided based on perceived skill-- since again, there was no qualifier round-- but it's possible we were :(
OSINT
It's worth mentioning that they put a heavy emphasis on OSINT (essentially, using public search engines). They may have had some plan for this, but nothing found online (the domain, LinkedIn posts, the AWS DNS records...) helped at all with the challenges. The portcosmar.com site wasn't even accessible outside of the competition LAN. Even after the event ended, I didn't hear about anyone actually using anything they found via OSINT.
Competition
Day 1: FTZ
Here's a network. Go!
Wait, crud, the Wi-Fi died. I guess our gigabit switches didn't improve the crap hotel access point throughput. Or maybe it was a misconfigured Cisco security feature? Still unclear. Everybody, send one person from each team up to plug into the switch. What, we forgot to run the DHCP server? We'll fix it for later rounds, start massscanning.
There was a CTFd instance that was supposed to be the canonical scoreboard, but all the challenges were very vague. There were no instructions, just got dropped onto a network, in an awkward circle of nerds.
I got into a camera (pictured), and some other devices on the network, most namely a router, all through default creds or CVEs. But none of them were flags? In the meanwhile, the storyteller walked around and let people know (indirectly, of course) that there would be a physical persistence challenge, for the blue team. Wait what, there's an active blue team? For how long? Where? What's their scope? This won't lead to me trying to plug in a RubberDucky right in front of them and getting firmly told to leave, will it?

It's still unclear to me, but I think we were supposed to pivot outside of the network via the router, then exploit a Windows box (maybe MS17-010 with a custom payload?) to get access to the actual ICS system or network (more like, notwork). That's a cool challenge, but it would've been really cool to know that was the objective. And if the network was functional.
Day 2: LNG, Shipboard Network, and Cargo Ship
As mentioned before, we were assigned the least difficult scenario, meant that if everyone solved their challenges, we would lose by default. Luckily that wasn't a problem, because we didn't haha.
Day two, Wi-Fi still busted, return to the nerd circle. Less surprising at this point, is that we need to break into a Windows Domain Controller before getting access to the SCADA/OT network.
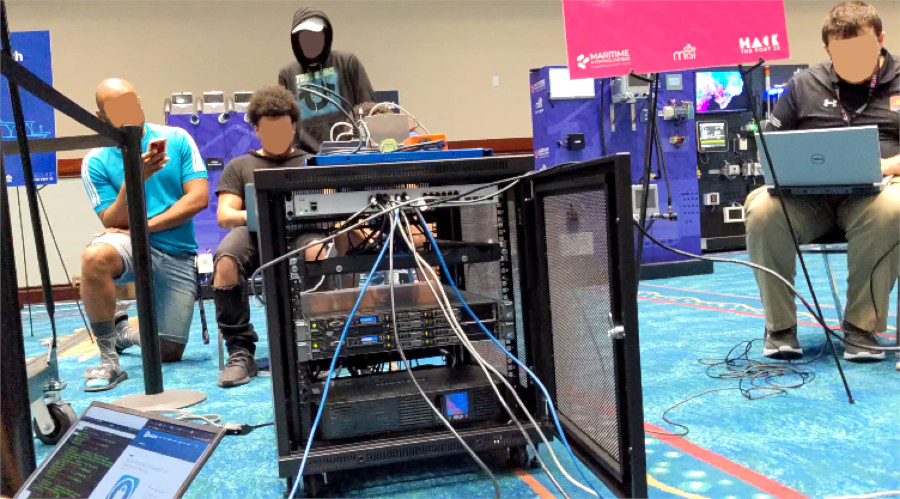
For as long as CrackMapExec would run, we tried bruteforcing passwords for the few usernames we got yesterday, and got nothing. As far as I know, nobody else solved it, or even got onto the OT network.
At the end of this day, there was another surprise challenge: the "cargo ship". Definitely the coolest setup, it was a kayak in a small pool, with some pumps on the top (presumably to simulate ballast pump stuff). If you controlled the pumps, you could make it tip over. Which is super fun!
So I plugged into a switch port as it opened up, two people solved it already. They handed out a Python script (rocktheboat.py) that controlled the pump system normally. They also posted a leaked picture of /etc/shadow, and a hint that the password for the admin was a popular Russian soccer team.
It seemed fairly easy to change the parameters in that script, or run it in a loop, to cause the boat to tip. I had no clue what the password would be useful for. The issue was that we didn't have the IP address. Well, we did have one, but it wasn't on our network. We were DHCP-assigned a 10.88.10.0/24 or something IP, and the address in the script was 10.88.13.2. With strict warning from the day before to not scan outside our network, I started nmappin' our subnet, while trying to avoid other competitors.

But nothing showed up! Thirty minutes into trying every scan known to man, I struggled through another hint of theirs, which was to set up (requires a Windows machine and an email sign-up) the proprietary OSI layer two Siemens network discovery tool. Running that, it showed the service running on the same IP that the script had. I thought it was some magic SCADA network protocol B.S., maybe a security feature, like we needed some value (maybe that password?) for the IP to respond to our traffic?
Our time ended before we got the script to work. Asking another competitor later, it turns out the IP was right all along (why hint at setting up that tool if you already gave out the address and script?!), and all you had to do was ignore the DHCP server and set your netmask to /16 (why would that be the solution when they were so strict about staying inside network assignments?!?!), then the script would work as expected. Since otherwise it would attempt to reach the LAN IP through the default gateway. :/
The guy running it was not the most friendly. I ran into him later and asked him if it the misconfigured DHCP was intentional, and he said yes, so whatever, I guess. Also, the /etc/shadow password leak wasn't useful for anything.
This was the last "real" day, so we had (unscored) fun afterwards with screwing around with the systems by plugging directly into them.
Day 3: Fun, Trains, Hospital
Day three of the competition was supposed to be an "All Star" day, where the blue teams compete against a team of only the "best" players from each team, for the whole day. I was kind of worn out after the past two days, but was elected by my team because they wanted to hit up the beach (just kidding, kind of). Like with most other things, turns out that this was not as strict as it sounded, and most of my team hung around for the whole day, and got free range access to mess with the systems.
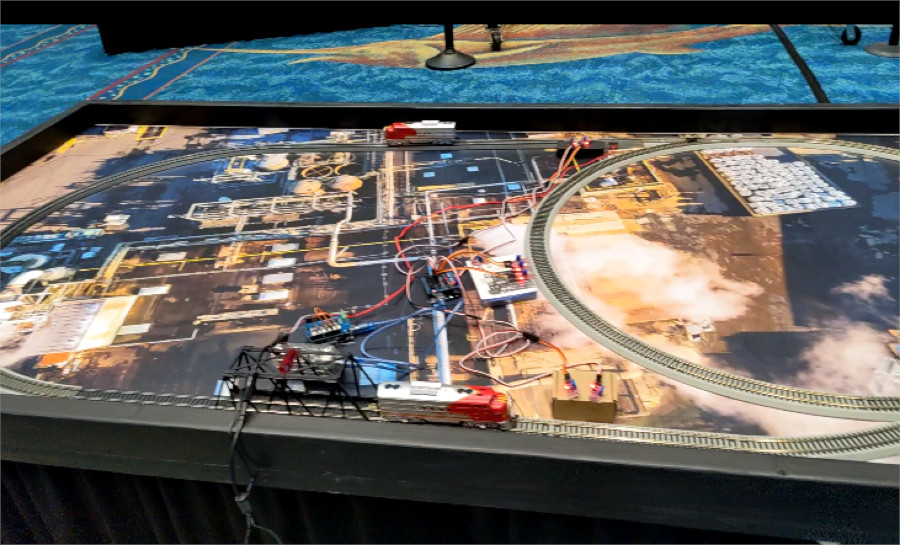
This was definitely the most fun day, and felt more like what the experience was supposed to be. I think there were some scored tasks, but we didn't really bother, since we were already in the can. I did get pretty far on the train challenge (some SSH port forwarding/VNC nonsense), until the organizer said it was broken and it was a WONTFIX.
Vibes
In these events, a consistent theme is that I really enjoy meeting and talking to other competitors, and this was no different. Chatting and working with the other "all stars" (AKA: abandoned by their teams) was definitely a highlight. I also was in the background of a news segment for the event.
I've never gone to the beach so much in my life. Focusing on enjoying the event, outings with my teammates, and the socialization mentioned above, greatly improved my experience. It was sunny, rainy, Florida-y. There were a ton of big boats that enjoy being looked at. Plenty of late hotel nights, trying to crank out preparations for the next day. Tons of neat, expensive hardware that we messed with. I treasure the experience.

Scores
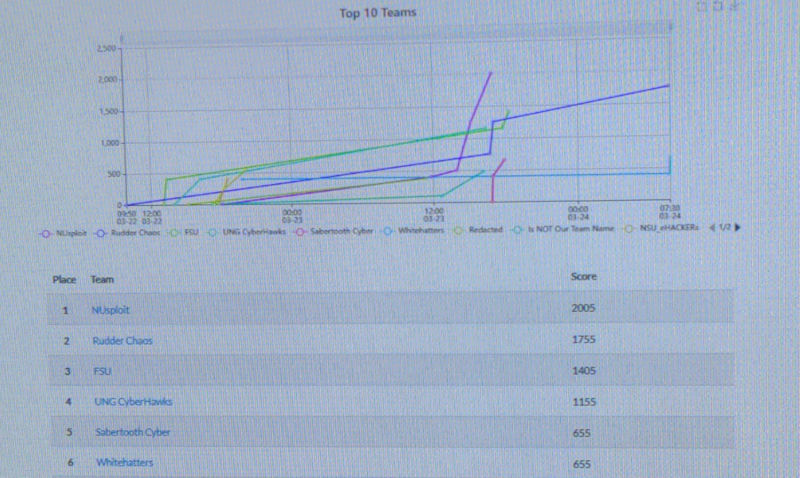
The main points came from the FTZ tasking (they added CTFd entries for compromising devices in the FTZ after we finished competing), the phishing PDF, your assigned scenario, rock the boat, the hardware backdoor, finding new 'vulnerabilities' (apparently some SaaS service dumped a bunch of private information when you visited a pretty guessable endpoint). Since we only successfully did the physical implant, we were not even close to placing, lol. NUsploit (Northeastern) for sure deserved the win though, they crushed every event that was solveable. Here's a non-final scoreboard:
Suggestions
Despite my criticism, the competition was a really neat experience that I would do again in a heartbeat. And they put the entire thing together in 90 days, which is impressive. Most of my suggestions, in any case, are about doing less.
What could be done better? In my opinion:
- Supporting remote teams while still "requiring" physical presence was a mistake.
- Kind-of-not-really relying on CTFd as a source of truth was a misleading decision, do all or nothing.
- Networking infrastructure was poor, stress test it before hand.
- Having a blue team haphazardly thrown in there was unfortunate. Do they have the authority to stop us from touching the systems? It should be clear what everyone's objectives and scope are.
- If you want to do legitimately "real world no rules"... then don't have rules.
So, I think this setup would have worked much better:
- Have all red teams compete at the same time, for eight hours each day of the conference. Change SCADA systems/scenario in scope each day. Remove the blue team.
This would solve all fairness issues with the existing setup, and give each team more time to explore the systems. A moderator would confirm successful manipulation of a system.
Anyway, fun event.